Si ayer os hablaba de una web que ofrecía servicios de
espiar WhatsApp, cambiar notas de la universidad,
hackear Facebook en un minuto, y demás servicios profesionales de hacking, hoy os traigo otra empresa de
Piratas Informáticos Éticos Certificados a los que podemos llamar (
PIEC) que también están al servicio del mejor postor. Lo curioso es que, a pesar de tener otro aspecto y otros contenidos, el correo electrónico de contacto es exactamente el mismo correo de
Gmail.
 |
Figura 1: Piratas Informáticos Éticos Certificados (PIEC) "for Hire"
|
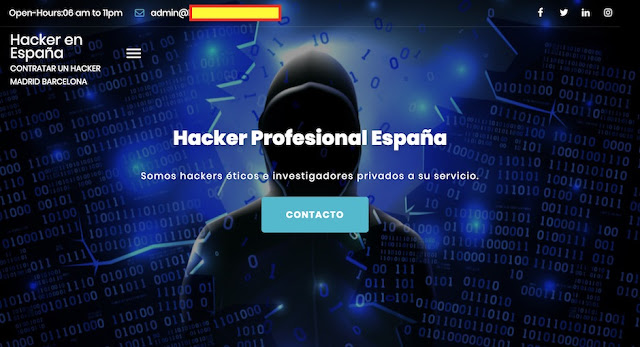 |
| Figura 2: Hackers Éticos e Investigadores Privados a su servicio |
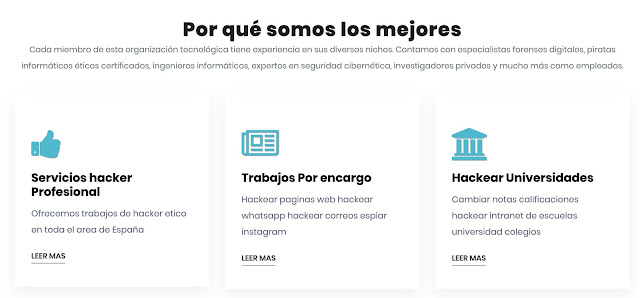 |
| Figura 3: Por qué somos los mejores |
Más o menos con el tipo de mensajes que me suelen llegar a mí demandando este tipo de servicios. Como en la web de ayer, también tenemos testimonios de clientes satisfechos con el servicio. No vayas a pensar que pagas por un mal servicio. Son Piratas Informáticos Éticos Certificados.
Entre los testimonios de clientes satisfechos está el de Carlos Pastrana contándole a todo el mundo que su mujer le engañaba y le era infiel, pero que gracias a este servicio de hackers profesionales - no sé si discretos - ya lo ha descubierto él y todo Internet. Y también Willians Miria que necesitaba unos hackers para piratear una web y que aquí le atendieron de maravilla.
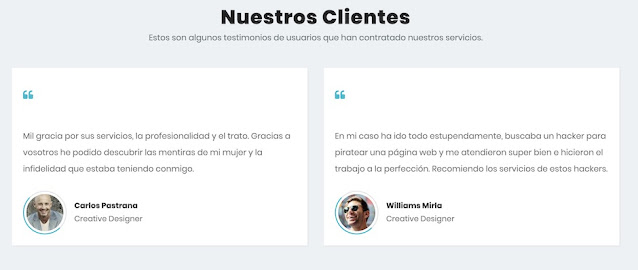 |
| Figura 5: Nuestros clientes |
Por supuesto, con utilizar un poco el
Hacking con Buscadores y tirar de Google Images vemos que la foto de
Carlos Pastrana es de un modelo nórdico utilizado en múltiples sitios de la red, que dudo mucho que sea uno de los clientes de
Hacking en España.
Me llama la atención que no se han molestado mucho en buscar o utilizar fotos de "This Person Does Not Exist" que dificultaría un poco más la búsqueda, pero está claro que esta web no está pensada para aguantar un análisis profundo, sino un que va dirigida a un público no tecnológico que está deseoso de estos servicios.
 |
| Figura 7: La foto de "Carlos Pastrana" es de un modelo |
Y el caso de Willians Miria es más peculiar, ya que es un emprendedor del mundo tecnológico que tiene hasta una empresa, y que es igualmente fácil de localizar con hacer una búsqueda por imágenes en Google.
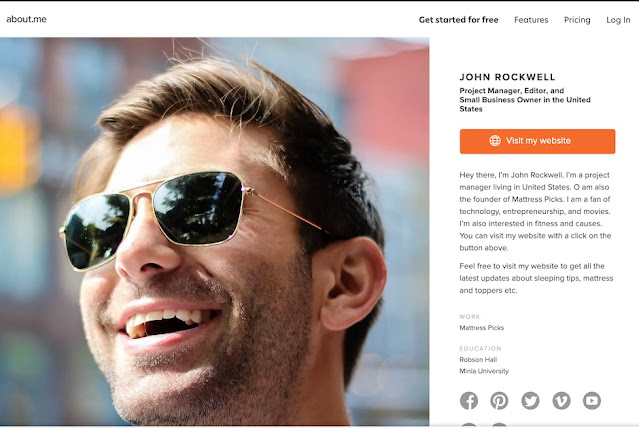 |
| Figura 8: La foo de Willians es robada de un perfil |
Por último, hay que remarcar la zona de contactos. Mientras que en la cabecera tenemos el correo admin del dominio como forma de contacto, y un horario de servicios muy
hacker de
6 A.M. a
11 P.M., como podemos ver en la
Figura 2, en la zona de contactos vemos el mismo correo electrónico
Gmail que había
en la web de ayer, un número de teléfono con un prefijo que seguro que no es de
Madrid, ni de
Barcelona, y un
FAX afortunado, que le ha tocado el
1234567 del mismo prefijo de esa ciudad
977.
 |
| Figura 9: Contacto de eta web |
Por supuesto, todos lo iconos de Linkedin, Twitter, Facebook, etcétera que aparecen la web no funcionan y no apuntan a ningún sitio. Es decir, la misma estafa de ayer para recoger dinero de todos esos que van por la vereda de Internet pidiendo a gritos meterse en líos. Ten cuidado con tu vida digital, como os he dicho muchas veces.

Related links
- Hacking Background
- Body Hacking
- Growth Hacking Madrid
- Hacking Meaning



































